How to Integrate LDAP with AEM ?
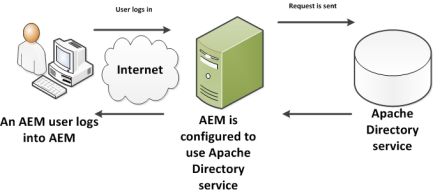
AEM - LDAP Integration LDAP (the L ightweight D irectory A ccess P rotocol) is used for accessing centralised directory services. You can achieve below vital things with LDAP integration The User accounts can be synchronised between LDAP server and the AEM repository. The AEM uses LDAP authentication to authenticate users, with credentials being passed to the LDAP server for validation. To improve performance, successfully validated credentials can be cached by repository, with an expire timeout. This helps reduce the effort required to manage user accounts as they can be accessed by the multiple applications. When a user/account is removed from LDAP server validation is no longer granted & access to the AEM is denied. The following are the AEM steps for integrating the LDAP and using it as your Single Sign On (SSO) source of truth for authenticating AEM Users. In order to have LDAP working with AEM, you need to create three OSGi configurations: An LDAP Identity Pro



